
The Threat Modeling Journey
A practical guide for organizations and their teams who are building a threat modeling program
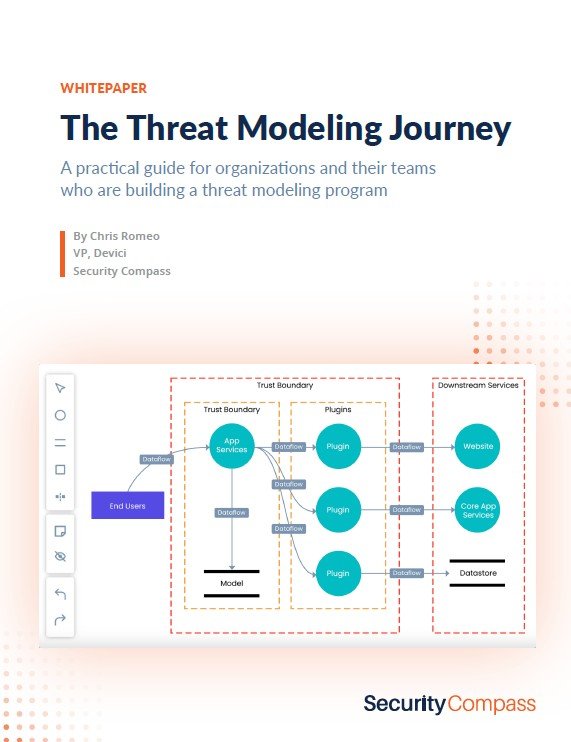
Most security professionals would like to see more threat modeling within their organization. Threat modeling is valuable because it identifies security and privacy issues at design time, leading to mitigation and vulnerabilities that never manifest in code. A feature or product that has been threat-modeled and mitigated well will have a higher reputation amongst those who use it because there are fewer security and privacy vulnerabilities to patch.
With this threat modeling journey, we hope to give you a perspective on how a program can mature over time. Threat modeling is a journey—not something you solve in a day, week, or perhaps even a year. However, it is solvable.
This Whitepaper from SecurityCompass is brought to you through harbourinsight.com. harbourinsight.com is a library of technology content for Business Professionals and Decision Makers. To receive more free reports from your favourite companies, please visit harbourinsight.com. Please read our Privacy Statement to learn how itdailyguide processes your personal data. Unsubscribe | Do Not Sell My Data